Anonymous Credentials in NYM

Since the dawn of civilization, identity has been essential yet problematic. From slaves and women deprived of rights to ethnic groups suffering genocide, identity often determines one’s access, agency and safety in society.
As life has digitized, identity matters more than ever. We rely on digital identities to participate in communities, transact, access services, travel, vote, speak anonymously, and go about daily routines.
Yet serious cracks plague traditional digital identity models. Vast troves of personal data harvested by governments and corporations centralize control and leave individuals vulnerable. What recourse do we have when identity systems themselves undermine human rights?
To address this crisis, visionaries are reimagining identity for the digital age. Rather than reposing power within centralized authorities, they seek to put individuals back at the center. Identities must enrich lives, not endanger them.
One such vision is emerging in the form of self-sovereign identity. With self-sovereign identity, users control their own credentials, choosing what data to disclose and when. Credentials guarantee rights rather than simply identify individuals. No single authority mediates identity.
Several key technologies enable this paradigm shift. Cryptography allows encoding credentials that individuals can selectively reveal yet remain unlinkable across contexts. Distributed ledgers let identities be anchored securely without centralized points of control. And zero knowledge proofs enable privately proving statements without disclosing unnecessary information.
NYM Technologies is pioneering the integration of these capabilities into a versatile platform for privacy-preserving identity. NYM combines a high-speed mixnet that hides metadata with an advanced anonymous credential system called zk-nym. Together, these technologies conceal communication patterns and transactions, while enabling private authentication.

Steps for obtaining and showing NYM credentials
By leveraging NYM’s comprehensive approach to metadata-resistant decentralized identity, we inch closer to a future where technology uplifts human autonomy rather than eroding it. A future where identity achieves its purpose — conferring rights, enabling participation, granting access. Not trapping, excluding and endangering.
This article illuminates the world of anonymous credentials and decentralized identity. We will explore the risks of traditional identity models and the paradigm shift offered by new approaches. We will demystify how anonymous credentials work, and examine NYM’s specific implementation. And we will traverse the frontiers of metadata resistance, as visionaries worldwide lay the stepping stones to the next era of digital identity.
I invite you to join me on this journey. At its end, you will understand the technology powering the identity revolution. But more crucially, you will grasp that we stand at a crossroads. Down one path, identity as a tool of control. Down the other, identity as an enabler of human rights. The choice ahead impacts nothing less than the soul of civilization.
The Ascendance and Evolution of Anonymous Credentials: A Cryptographic Odyssey
In the intricate landscape of digital identity and personal data management, anonymous credentials, also known as private credentials, minimal disclosure credentials, or privacy-ABCs, have emerged as a groundbreaking cryptographic solution. This innovative approach seeks to balance the imperative of identity verification with the paramount need for privacy.
The inception of the concept dates back to the 1980s when David Chaum, a trailblazing cryptographer renowned for his contributions to foundational privacy technologies such as mix networks and digital cash, first introduced the idea of anonymous credentials. Building upon his earlier work on blind signatures, which enabled users to obtain certified messages from issuers without revealing the content, Chaum envisioned a more comprehensive solution. Anonymous credentials take the principle of blinding a step further by encoding attributes certified by the issuer in a manner that keeps them concealed until selectively disclosed by the user.
The early implementations of anonymous credentials faced challenges. They involved complex cryptographic operations and exhibited limitations in proving relationships between credentials from multiple issuers. However, the subsequent decades witnessed a remarkable evolution driven by relentless research efforts.
Advancements in anonymous credential schemes have transformed them into more efficient, versatile, and scalable tools. Modern implementations have overcome the initial limitations, allowing for the encoding of multiple attributes within a single credential. Furthermore, they enable the proof of logical statements about credential attributes and the cryptographic binding of credentials while preserving anonymity.
NYM, with its zk-nym credentials, stands at the forefront of current research on anonymous credentials, epitomizing the cutting edge of this cryptographic evolution. These credentials not only integrate optimized cryptography but also introduce innovative features designed to elevate the standards of privacy in digital interactions.
The zk-nym credentials represent a harmonious blend of security and privacy. By leveraging advanced cryptographic techniques, NYM ensures that user data remains secure while enabling the selective disclosure of information when necessary. This approach aligns with the fundamental ethos of anonymous credentials, offering individuals greater control over their personal data and how it is shared.
The evolution of anonymous credentials signifies a crucial shift in the paradigm of digital identity management. It addresses the pressing concerns surrounding centralized identity systems, where security vulnerabilities and privacy infringements have become all too common. The cryptographic journey from the early, intricate implementations to the modern, sophisticated schemes reflects a commitment to refining and perfecting the delicate balance between identity verification and privacy preservation.
One of the key strengths of zk-nym credentials lies in their ability to encode multiple attributes within a single credential. This not only streamlines the verification process but also enhances the user experience, allowing for a more seamless and efficient interaction with various platforms and services. The flexibility and versatility of modern anonymous credential schemes contribute to their widespread applicability, making them a viable solution across diverse domains, from financial transactions to healthcare interactions.
Furthermore, the cryptographic advancements have enabled the validation of logical statements about credential attributes, empowering users with a tool that goes beyond mere identification. It allows individuals to assert specific attributes or qualifications without compromising the entirety of their identity, offering a nuanced and contextually relevant approach to information disclosure.
The cryptographic binding of credentials, while preserving anonymity, addresses a crucial aspect of data security. It ensures that even in scenarios where multiple credentials are involved, the linkage between them is cryptographically secure, reducing the risk of unauthorized access or manipulation. This not only safeguards the individual’s privacy but also fortifies the overall integrity of the credential system.
In conclusion, the journey of anonymous credentials from their conceptualization by David Chaum to the contemporary zenith represented by NYM’s zk-nym credentials is a testament to the resilience of cryptographic innovation. The evolution has not only addressed the challenges of the past but has also set the stage for a future where identity verification and privacy can coexist seamlessly. The zk-nym credentials, with their optimized cryptography and privacy-enhancing features, symbolize a new era where individuals can engage in digital interactions with confidence, knowing that their identities are secure and their privacy is respected. As we continue to navigate the complex terrain of digital identity, the evolution of anonymous credentials stands as a beacon, guiding us towards a more secure, transparent, and privacy-centric digital future.
The Need for Anonymous Credentials
In an era dominated by digital interactions, the need for anonymous credentials arises from the inherent privacy risks associated with conventional identity management models. The contemporary landscape mandates the establishment of one’s identity for participation in various facets of society, encompassing tasks such as acquiring a driver’s license, job applications, cross-border travel, accessing healthcare or financial services, and engaging on online platforms.
Typically, the process of proving one’s identity involves presenting official documents issued by governments, featuring attributes like date of birth, identification numbers, addresses, criminal records, and additional personal details. These fragments of identity are systematically recorded, tracked, and centralized in databases maintained by both public and private entities.
However, this conventional approach poses several challenges:
- Centralization Vulnerabilities:
Centralized repositories become attractive targets for hackers, leading to major data breaches. Incidents involving Equifax, OPM, Yahoo, Uber, Sony, and numerous others have compromised the personal data of billions of individuals.
2. Lack of Data Control:
With all identifying attributes consolidated in one location, individuals have limited control and transparency over the use, sharing, and exploitation of their data once collected.
3. Surveillance Implications:
Centralized data hubs facilitate extensive surveillance, granting authorities nearly unrestrained access to vast troves of private and personal information pertaining to citizens and consumers.
4. Correlation of User Activities:
The interconnection of various personal data points enables the correlation of user activities and transactions across different contexts, creating detailed profiles of behaviors and interests.
5. Elimination of Anonymity:
The centralized model eliminates anonymity, as all activities are intricately tied to real-world identities, undermining the concept of privacy.
The recurring vulnerabilities of centralized identity data silos, manifested through security breaches and privacy infringements, underscore the imperative for a transformative solution. Anonymous credentials emerge as a progressive pathway forward.
Understanding Anonymous Credentials:
Anonymous credentials represent a paradigm shift in identity management, offering a decentralized and privacy-centric alternative. In contrast to the conventional model, where a singular repository holds a comprehensive record of personal information, anonymous credentials distribute identity attributes across a network of verifiers without disclosing the specific details unless absolutely necessary.
Enhanced Security Through Decentralization:
By dispersing identity attributes, anonymous credentials mitigate the risk associated with centralized repositories. Hacking attempts become less lucrative, as compromising one verifier does not provide access to a complete profile, reducing the appeal for malicious actors.
Empowering Individuals with Data Ownership:
Anonymous credentials empower individuals by reinstating control over their data. Users determine when, where, and to what extent their identity attributes are disclosed, introducing a level of transparency and autonomy absent in traditional identity management models.
Privacy Safeguards Against Surveillance:
The decentralized nature of anonymous credentials impedes widespread surveillance. Authorities no longer have unrestricted access to centralized hubs of personal data, fostering a balance between security imperatives and individual privacy rights.
Contextual Anonymity and Behavioral Independence:
Anonymous credentials introduce contextual anonymity, enabling users to engage in various activities without compromising their overall identity. Behaviors and interests remain distinct across contexts, reducing the risk of comprehensive profiling.
Implementing Anonymous Credentials in Practice: The adoption of anonymous credentials requires collaboration between technology developers, policymakers, and end-users. Embracing advanced cryptographic techniques, such as zero-knowledge proofs, ensures the secure exchange of information without revealing the underlying data.
How Anonymous Credentials Work
Anonymous credentials allow users to prove certain facts about their identity in a privacy-preserving manner. Let’s break down how they work.
The basic roles involved are:
Issuer — The entity that certifies credentials, e.g. a government, bank, or organization.
User — The holder of the anonymous credential, who can selectively disclose attributes.
Verifier — The party who verifies credential attributes, granting access or transactions.
With anonymous credentials, issuers certify attributes about a user, like date of birth, nationality, account balance, etc. These certifications are stored in the credential.
However, the attributes themselves remain hidden from verifiers. Users choose which data to disclose, if any, via zero-knowledge proofs. These cryptographic proofs demonstrate that statements are true without revealing any unnecessary information.
For example, a bar could verify a user is over 21 without learning their name or actual date of birth. A bank could validate sufficient funds without seeing account balances. A duty free shop can confirm tourist status without passport details.
Selective disclosure allows proving only what is strictly required for the transaction, minimizing data exposure.
In addition to selective disclosure, anonymous credentials have other critical privacy properties:
- Issuer and verifier interactions are cryptographically unlinkable — issuers cannot tell when or where users present credentials they have issued.
- Multiple showings of a credential, across contexts or over time, remain unlinkable. Verifiers cannot determine if the same credential was shown previously.
- Users remain anonymous among the whole set of credential holders. There are no persistent identifiers that allow tracking users across services.
Together, these features prevent profiling users based on their verified attributes and credentials. Activities stay isolated in their respective contexts, rather than being linked into unified profiles.
Anonymous credentials thus shift identity from an oppressive system of control to an enabler of user privacy and autonomy. You prove what is needed for the purpose at hand, nothing more or less.
NYM’s zk-nym Anonymous Credentials
NYM Technologies has developed an advanced anonymous credential scheme called zk-nym to serve as a versatile privacy layer for its decentralized mixnet.

Users and services communicating privately through gateways and mixnet with 3 layers of nodes
NYM is building a next-generation metadata-resistant network that combines a decentralized mixnet for anonymous communication with anonymous credentials for private authentication and payments.
The mixnet shields internet traffic patterns from surveillance and correlation attacks by relaying encrypted packets via independent nodes. Anonymous credentials extend these protections to authentication events and financial transactions.
Together, NYM’s mixnet and credential scheme conceal who is communicating with whom, what services users are accessing, as well as transaction timings, amounts and account balances. This comprehensive approach aims to meet the scope of real-world privacy threats.
NYM’s credentials, issued by validators on the NYM network, are of two main types:
- Bandwidth Credentials — These encode a user’s proof of deposit into the NYM pool of tokens. The amount is exchanged algorithmically for network bandwidth capacity. Users show bandwidth credentials to NYM gateways to access the mixnet for a period of time.
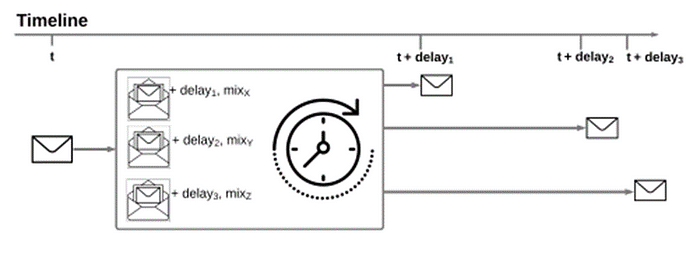
Continuous time mix
2. Service Credentials — These encode a proof of deposit for accessing paid services over NYM. A percentage fee goes to compensating NYM nodes, while the remainder represents a redeemable payment to the service.
Bandwidth credentials allow anonymous network access, while service credentials facilitate anonymous payments — together granting users the ability to privately use services integrated with NYM.
Service providers set their own access policies, with some accepting only bandwidth credentials while others require additional service credentials that may encode custom attributes or proofs.
For example, a whistleblowing platform could fund bandwidth credentials for users, while accepting sufficient service credentials as anonymous payments. This allows users to anonymously transact and communicate without any linkability to their real-world identity.
NYM’s credentials harness bleeding-edge zk-SNARKs and encryption schemes to enable advanced selective disclosure proofs, efficient multi-attribute credentials, and features that further enhance privacy:
- Issuing and verification transcripts remain unlinkable, preventing tracking.
- Expired credentials must be refreshed to stay within active anonymity sets.
- Credentials can be shieldedly merged, split, and recovered to break amount linkage.
- A global secret key in each credential binds credentials from various sources as belonging to the same user.
Together with its high-speed mixnet, NYM provides versatile anonymous credentials that unlock a new generation of privacy-preserving applications.
The Impact of Anonymous Credentials
Anonymous credentials have the potential to profoundly impact privacy, identity, and power dynamics in the digital age. Some of the anticipated effects include:
- Limiting data centralization — With personal data minimized and residing safely in user hands, massive centralized troves of information become less feasible and less attractive targets for hackers and exploitative parties.
- Restricting mass surveillance — Authorities must provide specific justification to access targeted data, rather than freely mining giant databases. Fishing expeditions and mass data grabs are obstructed.
- Empowering users — Users control their private data and make informed decisions about what to disclose and when. Personal data rights are enforced cryptographically rather than through policies alone.
- Enhancing cybersecurity — By reducing centralization of sensitive data, risks like mega-breaches are diminished. Selective disclosure also narrows the impact radius when breaches do occur.
- Boosting anonymity — Activities and transactions remain pseudonymous and unlinkable across contexts. Persistent real-world identifiers that enable tracking users across services are avoided.
- Protecting free speech — Association, exploration and expression are less susceptible to chilling effects from profiling, given the inability to connect speech to real identities.
- Strengthening privacy rights — Users are shielded from unchecked exploitation of their personal data by corporations, governments and other entities. Informed consent becomes enforceable.
- Preventing discrimination — Bias, exclusion and negative impacts based on profiling of personal data are obstructed, as selective disclosure prevents inadvertent exposure.
- Fostering innovation — New technologies and business models are unlocked as unhindered access to private user data becomes restricted by users themselves.
- Neutralizing coercion — With keys to personal data held only by users, others cannot improperly coerce consent to access private information. Right to erasure is absolute.
- Averting digital dictatorships — Centralized control over identity gives immense power that can be abused at scale in digital authoritarian systems. User-controlled identity distribution counters this.
- Protecting whistleblowers — Anonymous credentials allow sources to safely make disclosures to journalists without revealing their real-world identity even to the journalists themselves.
- Bolstering credit privacy — Oversharing of financial data leads to individual profiling and exclusion. Selective disclosure of credit attributes empowers individuals.
- Streamlining operations — Tedious identity verification processes can be reduced to simple cryptographic checks using credentials.
The list of potential impacts spans domains including finance, communications, social media, commerce, transportation, medicine, law, governance and more. Just as encryption guards content, anonymous credentials protect context.
As we continue rapidly digitizing more aspects of life, decentralized digital identity is essential to ensuring technology uplifts human rights rather than eroding them. NYM and similar initiatives are laying the groundwork for this vision today.
Conclusion
As we have seen, anonymous credentials hold enormous potential to preserve privacy and autonomy in the digital realm. By restricting unnecessary exposure, preventing correlation and abuse of data, and empowering users with control over their identities, anonymous credentials provide a crucial counterbalance to the privacy risks of traditional identity management.
NYM’s advanced zk-nym credential scheme represents the cutting edge in making anonymous credentials practical and scalable enough for extensive real-world use. zk-nym integrates optimized cryptography, efficient multi-attribute credentials, shielded operations for payment anonymity, and other innovations to deliver maximum privacy.
Crucially, NYM’s anonymous credentials seamlessly interoperate with its high-performance mixnet to offer comprehensive metadata privacy at the network level. This combination conceals who is communicating, what data is being accessed or transacted, as well as the underlying patterns of human behavior that emerge when activities are correlated.
By providing versatile anonymous credentials alongside its mixnet, NYM enables authenticated access to services with anonymity guarantees that protect users from profiling and surveillance, unlocking new possibilities for privacy-preserving applications.
As centralized platforms continue compromising user privacy through intrusive data collection and opaque exploitation, decentralized alternatives like NYM that put ethical principles into practice provide hope for a more enlightened path.
However, technology alone is not sufficient to bring about the change that is needed. As with previous paradigm shifts, from the printing press to social media, realizing the positive potential while averting the negatives will require wise policymaking as well as grassroots advocacy.
History shows that human rights are not something gracefully granted by those in power after polite entreaty. Rights are claimed through coordinated struggle, and then enshrined in enforceable laws and norms that distribute power more equitably across society. We must proceed with this truth in mind.
The road ahead will have many twists and turns. But the destination is clear: a future that protects privacy for all people as a universal right. Much work remains to build this future on technical, legal and social fronts. But solutions like NYM and anonymous credentials represent steps forward the privacy trailblazers of yesterday could only dream of.
There will always be those who seek to hoard power and control others. And there will always be those who resist, who believe in a more just vision. By coming together, raising our voices, and deploying technology as a great equalizer, we can overcome the forces that threaten privacy. The opportunity to steer the digital revolution toward human rights and freedom is ours for the taking.
NYM VPN website is now live, check it out here
Join our community: